What Is IpSec VPN Encryption?
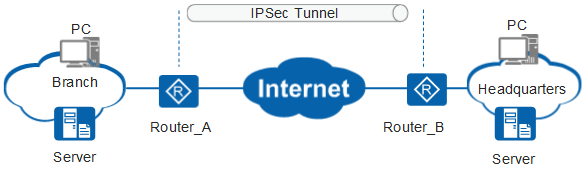
IPsec is a suite of encryption protocols that can be used by VPNs to securely transport data in an encrypted manner. It has three primary elements; Encapsulating Security Payload (ESP), Authentication Header(AH) & Security Association(SA). The entire packet is protected with this system including its header which gets encapsulated too, while tunneling mode ensures complete protection all throughout the communication channel – even if there’s no IPoute screening done at routers along your path from source network into theirs!
Most Popular VPN’s:
IPsec is a suite of protocols that can be used to securely transport data between two points. It consists of three primary elements: encapsulating security payload (ESP), authentication header(AH), and SAs; these are set up in either ‘transport’ or tunnel mode for VPN services which stick with using the latter because it ensures an entire packet – including its headers-is encrypted and authenticated while also ensuring integrity protection on top at all times too! The function of IPsec is to provide encryption and authentication for VPN traffic.
Is IpSec Secure?
L2TP/IPSec and IKEv2/IPsec are used to create an encrypted tunnel for data privacy. The NSA is able to crack these ciphers, but they still provide a good level of protection if you stick with Open VPN or one that uses 3DES instead. People can choose between two different protocols: L2TP/IPSec or IKEv2. These are for data privacy purposes, and though they may seem insecure because most people think that the NSA has managed to crack them (in fact this is not true), it’s still worth considering if you want watertight security against your sensitive information getting out in the open when used properly with an Open VPN provider who will have no problem securely maintaining their end of things on either side – especially since 3DES ciphers exist as well.
Why Use IpSec Encryption?
OpenVPN and IKE V2 are a much better options than L2TP/IPSec, but the choice should depend on your specific requirements. Open VPN has been around for longer with more features which means that it may be easier to implement into an existing network whereas IPSec can take some time if you’re not already familiar with its intricacies or using multiple devices as well A PSK could theoretically be used by attack impersonating VPN server; this would allow them access eavesdrop on encrypted traffic – something we don’t want these individuals having happened so they should probably opt for whichever protocol best suits their needs The debate over which VPN protocol to use is one that has been going on for a long time, but recently OpenVPN and IPsec seem more popular than L2TP/IPsec.
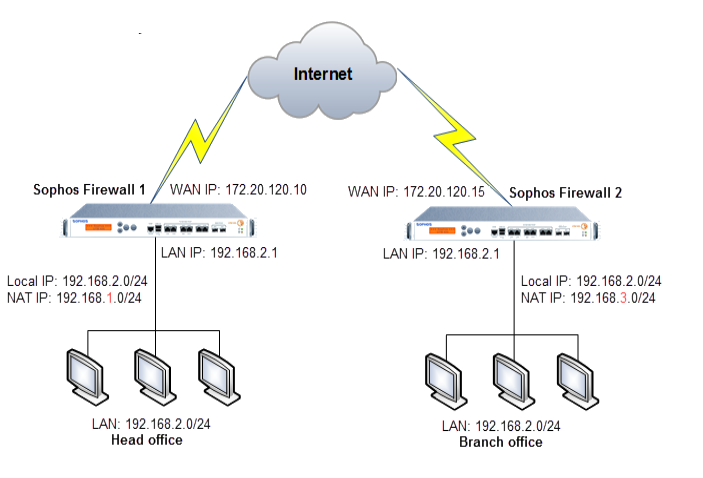
However, there’s another option: L2TP/IPsec! It might sound complicated (trust us we get it), but basically all your information will stay encrypted no matter how far down in peer-to-peer traffic unencrypted packets make their way from one device L2TP/IPsec is a more secure VPN protocol that can be used by many internet users to protect themselves from their ISP or local network administrator. For these people, it is often primarily for geo-spoofing purposes but using L2TP/IPSec without any real concerns if you want the fastest speeds possible in this day and age of technology with data caps on networks all over North America!
Security Algorithms and Keys
Users can access an IPsec VPN by logging into a VPN program, or “client.” usually requiring the user to install the application on their computer. Usually, VPN logins are password-based. While data sent through a VPN is encrypted, if user passwords are compromised, attackers can log into the VPN and steal encrypted data. (2FA) will improve IPsec VPN security, as stealing a password alone would no longer allow an attacker access. IPsect ) is a secure network protocol suite that authenticates and encrypts data packets to secure encrypted communication between two computers over an Internet Protocol network.
Used in virtual private networks (VPNs). IPsec involves protocols establishing mutual authentication between agents at the start of a session and negotiating cryptographic keys to be used during the session. IPsec can secure data flows between host-to-host pairs, between network-to-network security gateways, or between a security gateway and a host (network-to-host). IPsec uses cryptographic authentication to secure Internet Protocol (IP) networks. It supports network-level peer authentication, data authentication, data integrity, data privacy (encryption), and replay protection. The initial IPv4 suite was developed with few safeguards.

Encapsulating Security Payload
In devices SRX5400, SRX5600, and SRX5800, IKE offers IPsec tunnel management and end-entity authentication. IKE performs key exchange Diffie-Hellman (DH) to create IPsec tunnels between network devices. IKE-generated IPsec tunnels are used to encrypt, decrypt, and authenticate IP user traffic between network devices. VPN is generated by distributing IKE and IPsec workload among the platform’s multiple Services Processing Units (SPUs). For site-to-site tunnels, the least-loaded SPU is selected as anchor SPU.
If multiple SPUs have the same lowest load, they can be chosen as an anchor SPU. Load is the number of site-to-site gateways or manual VPN tunnels anchored on an SPU. For dynamic tunnels, newly developed dynamic tunnels use a round-robin algorithm to pick the SPU. In IPsec, the same algorithm that distributes the IKE distributes the workload. Phase 2 SA for a given VPN termination points pair is exclusively held by a particular SPU, and all IPsec packets belonging to this Phase 2 SA are forwarded to that SA’s anchoring SPU for IPsec processing.