What is Onion Over VPN?
Onion Over VPN is a privacy solution where your internet traffic goes through one of our servers, passes through the Onion network, and hits the internet only then. Currently, only the Onion Router browser can access the Onion network. NordVPN doesn’t need to download a special browser. Everything you need to do is connect to a VPN server onion. Your internet traffic would then be routed across the Onion network without additional applications. You can, of course, also connect to our standard servers and use Tor as usual.
What Is “Onion” In The First Place?
Onion is a network of relays/servers designed to disguise your identity by encrypting your Web traffic. Therefore, it’s quite similar to VPN services. However, make no mistake – Onion and VPNs present two very different sets of technologies. What makes them similar is their end goal—and that would be digital privacy.
There are many differences between the two, and those differences span across methodologies used conceal Internet traffic . Routing traffic through “Onion” relays is free , so anyone can do that; however everyone needs an ISP with support for IPv6 protocol in order to access these servers from outside TOR network . The only requirement for accessing “onion” server You should avoid using pronouns such as ‘ Onions, also known as Tor (meaning “The Onion Router”), is a network of relays/servers designed to disguise your identity by encrypting your Web traffic. Like VPN services however, make no mistake; Onions and VPNs present two very different sets of technologies with their own unique methodologies that separate them from one another. The most notable difference between the two would be price: while onion routing is free for anyone who wishes to do so there are additional advantages when using an encrypted Virtual Private Network such as added security features like DDoS protection and malware blocker’s or better speeds than those offered through standard HTTP encryption protocols Onion routing disguises web traffic in several layers making it difficult for ISPs or other third parties trying to
What is Onion, TOR or Network?
Onion routing is very similar to a virtual private network in that they both encrypt data and send it anomaly so you cannot trace the data back to its source. Unlike a virtual private network, which requires you or your company to pay for it, Onion networks operates by using free services from large numbers of volunteer servers dedicated entirely towards this system’s cause. When sending information through these nodes, each piece gets shipped off into different directions only one layer at a time until finally arriving at their destination with all original layers intact without any tampering along the way! Onion routing is a free service that operates by using multiple volunteer servers. Data gets encrypted and sent to these nodes in an anonymized manner so you cannot trace the data back to its source.
Unlike a virtual private network, this system does not require payment from either users or companies who use it which makes for fast growth of Onion networks worldwide since even small businesses can afford it without worrying about financial restrictions. Communication over the Internet is typically done by sending data in packets. All nodes on a network are visible to each other, but only one node can send information at any given time. This means that if someone intercepts your packet of information, they will be able to identify you as the last person who sent it along its route before them…While the worldwide web gives us access into topsoil-level layers of o Information associated with internet protocols lies below this baseline level and forms what we know today as “the Dark Web” or deep recesses accessible via Tor networks.” Onion routing is a technology used to anonymize the sources and destinations of data packets on computer networks. It’s one way that you can access information without revealing your true location or identity throughout the process.
Onion routing only operates using HTTP, which stands for Hypertext Transfer Protocol, because it allows users to visit web sites anonymously through an encrypted network with multiple nodes in between where each node carries part of this traffic before passing it onto another layer so no one person in particular has f that have been passed along from user . The darknet refers specifically to hidden services within onion routers whereas other websites are hosted either openly or not visible at all..
How To Use Onion Over VPN?
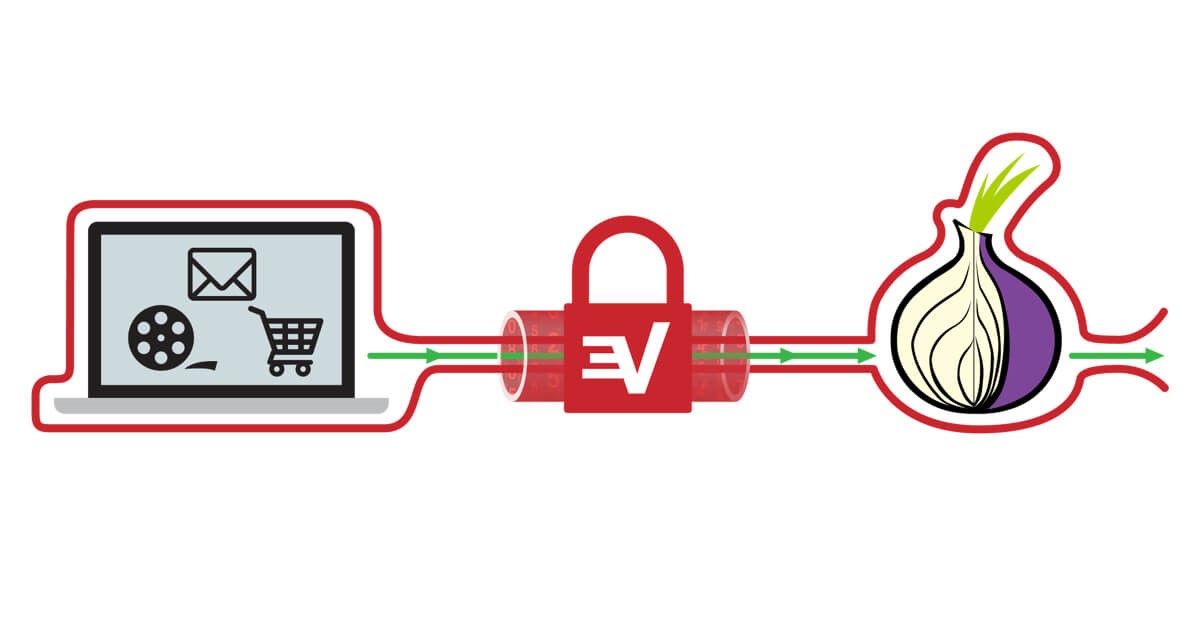
To access the Onion network with VPN, you will have to download Tor. The process involves downloading then connecting to a regular VPN server. Once this is done and browsing begins, your traffic routes through the servers in layers before reaching its final destination . To avoid these steps , some providers offer an onion over vpn connection that allows routing without having tor browser installed on their system The process for accessing the Onion network with a VPN is slightly complicated.
First, you need to download and install Tor browser on your device (follow this step-by-step guide). Then, connect it to one of many regular VPN servers that allow onion routing . Finally, open up any website; your traffic will be routed through the anonymizing Tor network before reaching its final destination Generally , you can only access the Onion Network with The Tor Browser . Hence , You Will Have To Download the browser For The Process To Work … After connecting to a regular vpn server…
Is Onion Over VPN Safe?
In such a network configuration, the major vulnerabilities can fall on separate intermediaries: either VPN or Onion network. In VPNs, not all of them are made equal. You must be sure that the service is no-log VPN service. Don’t take the word of the provider. Records of failure to comply with law enforcement, third-party audits will basically show you can trust a service. If the VPN holds your logs, your statements are invalidated and this is one of the possible challenges to your privacy.
The only drawback in the Onion network is that it’s community-based, and anyone can set up a Tor node. It means some hackers-managed rogue nodes can potentially spy on you. De-anonymizing the relation isn’t as cookie-cutter. It will possibly need funding only for national governments. While a theoretical possibility, it’s a point to consider. Using Onion in combination with a VPN, the best part is that the privacy rests on two different individuals. Even if there are risks and possible failure points, the chain is longer and there are more protection features than you would get if you used the service alone.

The VPN also encrypts some of the internet traffic that the Tor doesn’t encrypt, e.g. ICMP. Plus, if you’re using the Tor network, your ISP will claim you’re using it. With a VPN, saying becomes difficult.
How Do the VPN and Onion Network Work Together?
If you live in a country with strict censorship laws or want your web browsing data secured, an onion over VPN will provide the privacy you need online. Outside, this precaution can seem overkill. But it actually offers an invaluable surveillance network. While you may be familiar with a virtual private network idea, when people use it in combination with an onion network, many people get confused.
g experience. The key difference between the services is that only when routed over standard HTTP web traffic, Onion offers anonymity. When using Onion over VPN, it offers an additional protection layer when browsing the site. Before we fully understand the definition, however, we must first ensure that we understand the broken down components, how a VPN and Onion network is and how they work together.
Why is it Important to Try and Remain Anonymous Online?
When you use an Onion over a VPN service, any internet operation you engage in will first go through the private network server, then go through the Onion network. This double encryption method makes tracing back to you practically impossible for anyone. Unfortunately, many people live in countries that use internet using strict, oppressive censorship rules.
Although the Onion network may like a useful way to circumvent these rules, your Internet service provider will still be able to see that you used a TOR network to exchange details. The simple fact you used an Onion network in the strictest company might be enough to target or prosecute you. Moreover, some governments may penetrate the Onion network, deploying thousands of relay points that can catch bits of decoded data as it arrives. Thus, Onion’s network includes several major defects.
But when you use it in combination with VPN, it becomes much safer. The main explanation for this improved protection is that a virtual private network won’t let the Internet service provider know you’re using an Onion network. Furthermore, after submitting confidential information, the “paper trail” cannot return to you. Using Onion over VPN, the service protects your web protocol address.
Why Use this Feature?
Now that we know the answer, what’s Onion over VPN? ‘Let’s discuss why we should think about anonymity online. For many journalists, political activists and artists living in countries with strict censorship rules, staying anonymous can mean life-to-death difference. A device like Onion over VPN becomes invaluable as it is impossible to trace back to source. However, circumstances involving restrictive governments aren’t the only reason anyone needs the service’s additional protection.
Though we put much trust in internet security, this belief is misplaced. From an infrastructure standpoint, the internet was never supposed to become the global marketplace it is. It contains a number of holes where sketchy people can access your data. If you know it or not, corporations lawfully and unlawfully mines the things you look up while on the internet. Corporations like Google sell your details to marketers online, so they can target you with personal advertising.
Although this act may not seem like a big deal, it’s massive consequences. Whatever you scan, whether it’s private medical records or compromising websites, hackers can reach reasonably easily. A VPN guarantees hackers cannot access your data when sending it. Hopefully this article helped you figure out what Onion’s about VPN. We assume the service offers an invaluable backup layer when browsing online. Although not everyone cares about their protection online the same amount, it remains crucial. If you know it or not, you have a lot of online personal details, whether it’s your social security number, bank information, or personal information.
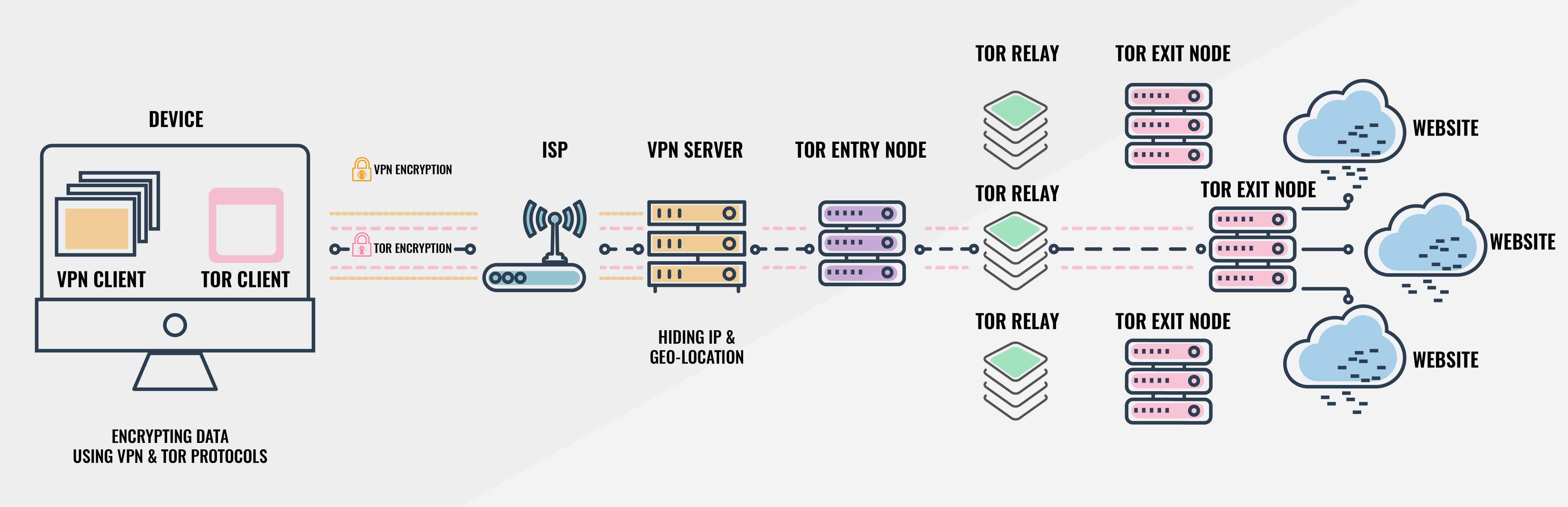
If you’re not careful, you could stolen your whole identity, or worse. Onion network over VPN makes hackers even harder. @11@ Connecting to the Tor network with the “Onion over VPN” feature prevents your home IP address from being accessible to the Tor node you connect. Using “Onion over VPN” often prevents your ISP from knowing that you’ve linked to the Tor network, since they can only see that you’ve connected to your usual VPN provider. For Onion over VPN connections, your computer connects to your VPN server and connects to the Tor network via an entry node. When in the Tor network, the link is passed through a relay node and then exit the network to connect to the target website.
Think of it as a tube to enter your target location. Using three randomly selected nodes in the Tor network is designed to restrict each node’s available information. The entry node just knows your VPN provider’s IP address, in this situation. The exit node knows only the site-connected URL. The relay node is used to ensure that entry and exit nodes never interact directly, making it much harder to de-anonymize any network traffic compared to one or even two chained VPN servers.
Using the Tor network has a performance effect due to using four VPN servers, including the server of your VPN provider. As such, it is not really appropriate for daily usage, just use the setting “Onion over VPN” if you actively want to access secret onion services. You’ll find visiting websites a bit slower than otherwise. @12@ VPNs remain widely used as data protection and user privacy tools. Yet, as predicted, there are many providers and many choices within those providers – so buyer uncertainty will reign. A virtual private network is the secure, private connection between your device and destination.
When working with VPN servers, options extend. There are a range of server types to choose from; regular servers, double VPN servers where the data is encrypted twice, ‘Onion over VPN’ involving the Onion network, dedicated IP servers, P2P servers, and obfuscated servers. Obscured VPN servers are increasingly becoming a useful tool, particularly in countries with limited internet access. What are blurred VPN servers? How are they working? What are your options?


